Security Consulting
Best-in-class security consulting provides peace of mind in today’s sophisticated IT security environment. With JAS, senior experts will thoroughly assess your operations and identify potential security gaps. Existing technology infrastructure can be measured against specific threats and the aggregation of risks resulting from complex inter-relationships among organizations and technologies.
Have you outsourced portions of your IT to save money, find competence or better focus on your core competencies? JAS experts will evaluate both internal and external systems. Our security assessments and planning multiple IT dimensions across the enterprise, including:
- Organization and whether the hierarchy, lines of communication and talent match the security requirements imposed by the risk landscape
- Strategic approach to core competencies and make/buy decisions
- Wholistic security intelligence, including threat and vulnerability assessment.
- Rigorous testing of your security program through penetration testing
- Vendor selection processes
- Vendors’ competence in security planning and execution
- Vendors’ strategic approach to make/buy decisions
- Aggregation of risks facing your firm
Attempts to mitigate risk through a diverse outsourcing strategy can be defeated when vendors rely on a common source. In some cases, your vendors may not have addressed the aggregation of risk, and present a likelihood of failure or harm to your organization.
How Security Efforts Might be Defeated
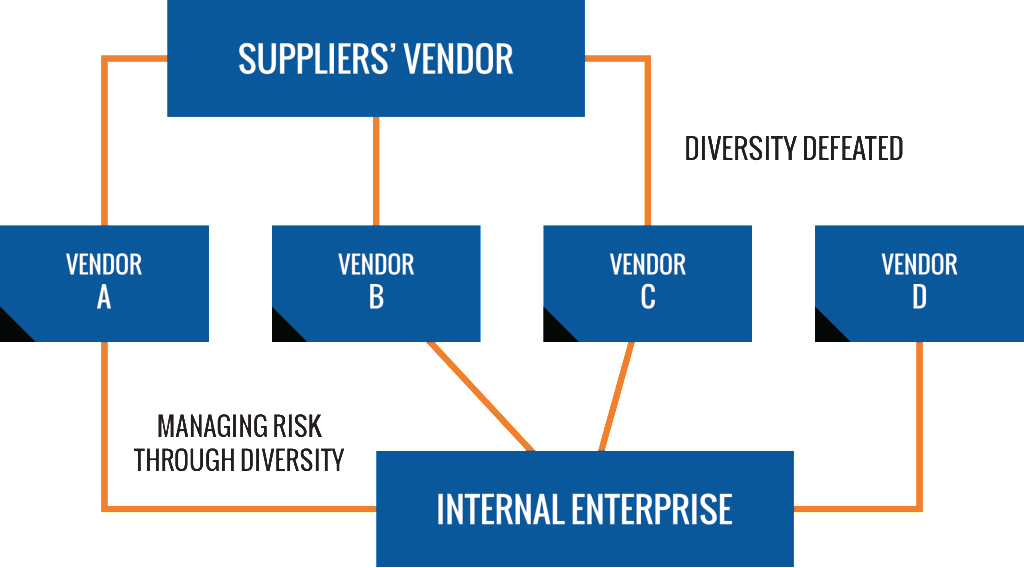
JAS understands the threat aggregation of risk poses to your organization and will investigate whether your technology partners have outsourced portions of their work to a common source.
Our security experts will also recommend staffing skill inventory adjustments and organizational structure changes to align talent with the security approach that is right for your business.
One of the things that sets JAS apart from IT security firms is that we take the time to understand your business, its pressures and your restrictions. Our recommendations are tailored to meet your time, resource and budget constraints, while equipping your organization with the best possible security measures.
